Two New DNS Record Monitoring Features

We’re excited to announce two significant enhancements to DNS Check: DNS Record Flapping Detection and Extended Notification History. These features streamline the troubleshooting process for recurring DNS resolution errors and reduce repetitive notifications.
DNS Record Flapping Detection
DNS record flapping occurs when a record rapidly alternates between passing and failing states. With our new feature, DNS Check identifies records that change state six or more times within two hours as flapping. This proactive detection serves two primary purposes:
- Notification of Flapping Issues: DNS Check will alert you when flapping is detected, enabling you to investigate and address potential problems rapidly.
- Aggregated Notifications: DNS Check consolidates flapping alerts into a single email per hour for users with immediate email notifications enabled. This approach prevents an overwhelming number of emails during periods of instability. There are a few caveats to this behavior. See our FAQ entry for details.
Common causes of DNS record flapping include:
-
Inconsistent Responses from Authoritative Nameservers: Different nameservers may return varying results for the same query, often due to misconfigurations.
- Geolocation-based Routing: DNS Check queries from multiple global locations, which can trigger discrepancies in DNS responses from CDNs and load balancers. To address this:
- If monitoring a CDN or load balancer record, configure it as a load balancer record and specify all potential IPs or hostnames that your CDN or load balancer could return. DNS Check will consider the record passing if any subset of the expected results are returned.
- Alternatively, set a specific nameserver for DNS Check to query to ensure consistent results from a deterministic IP address.
- Connectivity Issues: These can cause a record to alternate between passing and failing with ServFail errors.
By detecting and alerting you to flapping records, DNS Check empowers you to maintain the stability and reliability of your DNS configurations.
Extended Notification History
Understanding the history of your DNS records is crucial for effective troubleshooting and analysis. We’ve expanded our notification history retention for Enterprise accounts to 365 days, allowing for a full year of state change tracking. Professional accounts retain 90 days of history, while Basic accounts maintain a 7-day history. This extended access enables you to observe long-term patterns, investigate past incidents, and maintain comprehensive records for auditing purposes.
These enhancements reflect our commitment to providing robust and user-friendly DNS monitoring. We aim to empower you with the tools to maintain an optimal DNS configuration by offering detailed insights into DNS record behavior and extending historical data access.
For more information on these features and how they can benefit your organization, visit our Features page.
Continue reading Two New DNS Record Monitoring Features »
Capacity Expansion

We will migrate DNS Check’s infrastructure to more powerful hardware on Saturday, July 24. The maintenance window will begin at 12 am UTC and end at 1 am UTC.
We anticipate that this migration will cause 10-15 minutes of downtime for our website and API endpoints. Monitoring of some DNS records will also be delayed by up to 15 minutes.
The upgrade will make DNS Check’s website snappier and increase the number of DNS records we can monitor. We’ve grown steadily since our last major hardware upgrade in 2018. We still have spare capacity from the 2018 upgrade but are upgrading now to ensure that we stay well ahead of the growth curve.
If you’re using our API for DNS record monitoring, then we recommend scheduling a maintenance window within your monitoring system that runs from 12 to 1 am UTC on Saturday, July 24.
Feel free to contact us if you have any questions.
Continue reading Capacity Expansion »
DNS Monitoring Improvements
Happy New Year! We want to kick off 2021 by announcing some improvements to DNS Check.
1. Extended the Notification History
When troubleshooting an intermittent problem or flapping record, it’s useful to see what failures occurred in the past and look for patterns. DNS Check maintains a log of the notifications sent for each monitored DNS record to support that type of troubleshooting. Each record’s log can be viewed by clicking its History button.
Here’s an example report:
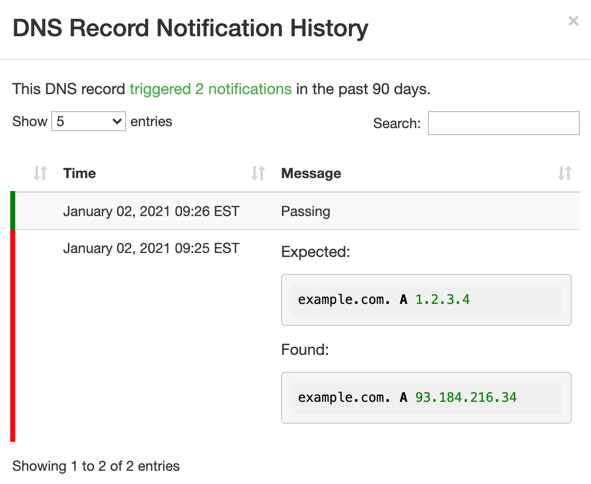
The log used to be maintained for 30 days for paid accounts, but we recently increased the retention period to 90 days.
Free accounts can also view this log, but only for the past 7 days.
The Troubleshoot DNS Records page has more details on this feature.
2. Added Support for Monitoring More DNS Records
We added four new subscription options to the checkout page to monitor up to 3,000 DNS records. Previously, the largest available package on that page had a 1,0000 DNS record limit.
We’re also able to create custom packages for monitoring more than 3,000 DNS records. Get in touch with us if you’d like a custom quote.
3. Made the Zone File Importer More Robust
DNS Check offers the option of importing entire zone files for monitoring. This system worked for properly formed zone files, but some DNS hosting providers produce malformed zone files that can cause issues, like making individual records unreadable. Another common problem is omitting the zone file’s $ORIGIN, making relative references like @ meaningless.
We’ve enhanced the zone file importer’s “Autocorrect syntax errors” option to fix more types of zone file issues. The enhancement was significant enough to warrant turning the option on by default. It was off by default before.
The Monitor DNS Records page shows how to access the zone file importer.
4. Made the Check Frequency Configurable
We added the ability to customize how often DNS records are checked. Each DNS record group now has “Check frequency” settings that can be set to any of the following:
- Every 5 minutes (the default)
- Every hour
- Paused
Previously, all DNS records were checked every 5 minutes, and there wasn’t any way to pause checks.
5. Added a Status Page
Finally, we’ve created a status page at status.dnscheck.co. Moving forward, we’ll post notices about upcoming maintenance there. If any services experience downtime, we’ll also document them on the status page. Feel free to subscribe for status updates.
That’s it for now. More improvements are coming in 2021, and we’re looking forward to sharing them with you.
Continue reading DNS Monitoring Improvements »
Upcoming Maintenance
We’re going to replace some of the hardware that runs DNS Check’s website on Friday, May 8th, between 4:15 am and 12:15 pm UTC.
A few minutes of degraded performance is expected towards the beginning of this window.
Website downtime is possible, but not expected. If downtime does occur, then it’s expected to last approximately 5 minutes.
If you’re using our API for DNS record monitoring, then we recommend scheduling a maintenance window within your monitoring system that covers this window.
Feel free to contact us if you have any questions.
Continue reading Upcoming Maintenance »
Upcoming Maintenance
We’re going to perform software updates to DNS Check’s website on Sunday, December 30th between 11:00 pm and 11:30 pm UTC. We anticipate that the updates will cause 5-10 minutes of downtime for our website.
If you’re using our API for DNS record monitoring, then we recommend scheduling a maintenance window within your monitoring system which covers this window.
Feel free to contact us if you have any questions.
Continue reading Upcoming Maintenance »
Monitoring DNS Records for Wildcard Values
Back in 2016, we added support for monitoring wildcard DNS records. Wildcard DNS records are used to serve requests for otherwise non-existent domain names. For example, if you created a wildcard record for *.example.com, but not a foo.example.com record, queries for foo.example.com would receive the IP addresses specified for *.example.com in response.
Today we’re pleased to announce that we’ve extended our support for using wildcards in DNS records monitoring. DNS Check now allows you to specify a wildcard (*) in place of some DNS record values, such as an A record’s IP address to indicate that any value is acceptable, but the record must exist.
Wildcard values are supported in the following areas:
- A and AAAA records may have an IP address of * specified.
- CNAME records may have a value of * specified to indicate that they may point to any domain.
- MX records may have an exchange of * specified to indicate that any exchange is acceptable.
- NS records may have a value of * specified to indicate that any nameserver is acceptable.
- PTR records may have a value of * specified to indicate that any value is acceptable.
Here are a couple of example use cases:
Load Balancer Monitoring
Suppose you’re using a load balancer to split requests for your website - www.example.com between a pool of web servers. The pool is dynamic, so you don’t know ahead of time which IPs will be returned in response to each query, but you want to make sure that at least IP is returned.
You can do that by creating a new monitored DNS record with an IP address of *:
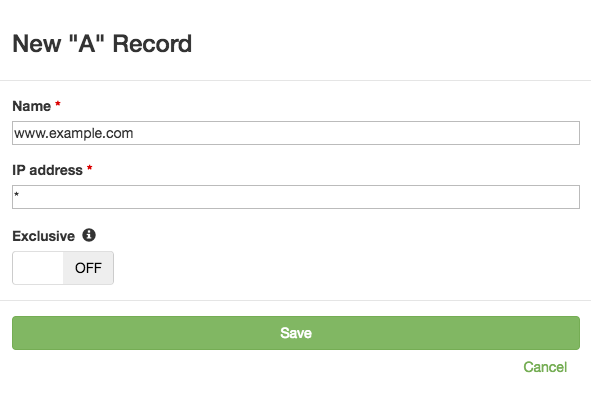
In the above screenshot, www.example.com would pass as long as one or more IP addresses are returned in response to each query.
Toggling the above form’s “Exclusive” tag on would enforce a requirement that only one IP address is returned.
Similarly, toggling the above form’s “Exclusive” tag on, then creating a second identical monitored DNS record would enforce a requirement that exactly two IP addresses are returned.
G Suite DNS Record Monitoring
For our second example, suppose that your organization uses G Suite, and you wish to monitor the CNAME record that they asked you to create.
; Name Type Value
mail.example.com. CNAME ghs.googlehosted.com.
That’s simple enough. You can just create a CNAME record in DNS Check:
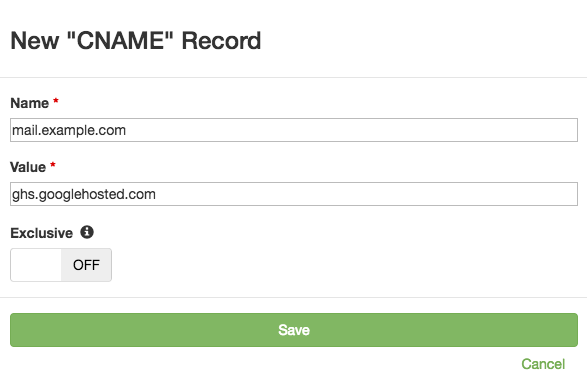
Once the above monitored record is created, DNS Check will automatically check it every 5 minutes, and notify you if it changes.
But what about the ghs.googlehosted.com record that we’re pointing to? How do we know that it’s working?
Normally monitoring ghs.googlehosted.com would be difficult because Google could return any of their IP addresses in response to each query. With wildcard DNS records, you can just tell DNS Check that you want to make sure that ghs.googlehosted.com returns at least one IP, but don’t care which one it is:
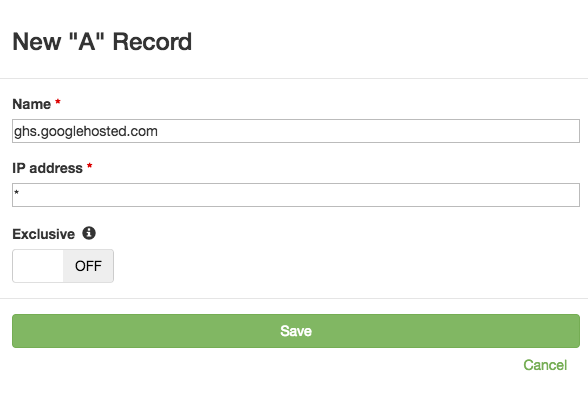
Have any questions about how to use wildcards in your DNS record monitoring? Contact us. We’re happy to help.
Continue reading Monitoring DNS Records for Wildcard Values »
Upcoming Maintenance Rescheduled
We’ve moved the Sunday, February 25th maintenance window that was announced in the previous post to take place on Monday, February 26th between 16:00 and 17:00 UTC.
The maintenance window was rescheduled so that mitigations for the Spectre and Meltdown vulnerabilities can be put in place at the same time as the hardware upgrade.
We anticipate that this maintenance will cause 5-15 minutes of downtime for our website.
If you’re using our API for DNS record monitoring, then we recommend scheduling a maintenance window within your monitoring system which covers this window.
Feel free to contact us if you have any questions.
Continue reading Upcoming Maintenance Rescheduled »
Upcoming Maintenance
We’re going to migrate DNS Check’s website to new and more powerful hardware on Sunday, February 25th starting at 1:00 am UTC. We anticipate that this migration will cause 5-10 minutes of downtime for our website.
If you’re using our API for DNS record monitoring, then we recommend scheduling a maintenance window within your monitoring system which covers this window.
Feel free to contact us if you have any questions.
Continue reading Upcoming Maintenance »
Integration Updates
We just finished refactoring the code that we use for integrating DNS Check with services like Slack and PagerDuty. It felt good to take some of the bespoke code that had accumulated over the past couple years as integrations got added in and generalize it.
These updates will allow us to more easily add and update integrations in the future.
You shouldn’t notice any difference in how existing DNS Check integrations work.
Feel free to contact us if you have any questions.
Continue reading Integration Updates »
Upcoming Maintenance
We’re going to migrate DNS Check’s website to new hardware on Thursday, October 13th starting at 12:00 am UTC. We anticipate that this migration will cause 5-10 minutes of downtime for our website.
If you’re using our API for DNS record monitoring, then we recommend scheduling a maintenance window within your monitoring system which covers this window.
Feel free to contact us if you have any questions.
Continue reading Upcoming Maintenance »
Subscribe via RSS